Malware and Your Industrial Control System
Most of us have had the unfortunate experience of getting malware on our personal computers. Removing some of these nuisances can be as easy as running a simple virus scanner. Others can maliciously take over a computer and make it impossible to use. While this malware is troublesome on a home computer, it can be disastrous to an industrial control system (ICS). With access to an ICS, a threat actor could take down critical computers and cause costly downtimes, or they could go a step further and take control of equipment which could result in property damage or injury to personnel.
According to a recent Booz Allen Hamilton report, the top three industries targeted by malicious software attacks in 2015 were critical manufacturing (33 percent), energy (16 percent), and water and dams (11 percent). The majority of these attacks came from Nation-State groups, which are groups that operate under the direction of, or in coordination with national military and intelligence services. The top offending Nation-States are Russia, North Korea, Iran, and China. Of these countries, China is the most likely to attempt to gain access on U.S. networks primarily with the intent of intellectual property theft. North Korea is the most likely to attempt a destructive type of attack.
According to the report, ICS operators reported 50 more security incidents in 2015 than in 2014, an increase of 20 percent and more than any year prior. Taking a step back, this information isn’t all that surprising. Industrial control systems are becoming increasingly connected in order to allow data collection and system monitoring. This unfortunately also creates an increase in the number of targets of opportunity. In many cases the benefits of connecting these systems justify the risks, but it is necessary to be aware of the potential dangers when designing the operational technology (OT) network that the ICS resides on.
System security is not measured in black and white terms of secure/not secure, but is measured on a “more secure/less secure” continuum. The only way to know your systems are protected from outside intrusions is to create an “Air Gap”, i.e. disconnect the network completely. However, to be completely disconnected is not an ideal solution in most cases. An understanding of the risks that are involved and an attempt to mitigate those risks is necessary when connecting the IT and OT networks.
Mitigation of risk involves more than simple IT steps, like setting up a firewall and applying patches. It must also involve creating an incident response plan and training personnel. It can be thought of as being similar to protecting against fire damage. You build a building to prevent a fire from happening, but you still install exit signs, train people on fire prevention, install fire extinguishers and sprinkler systems, and inform staff of what to do and how to act quickly if a fire does start.
Examples of risk mitigation steps to take on the IT side include proper firewall configuration and keeping system patches updated. Also, a planned network architecture with segmentation is a good way to isolate intrusions to one area. Since the IT network is an easier point of attack than the OT network, it should be viewed as a potential threat entry point to the OT network. There should be a “demilitarized zone” (DMZ) between the OT network and the IT network to prevent any intrusions from spreading from one to the other. All traffic between the IT and OT should terminate in the DMZ. See the Purdue model below.
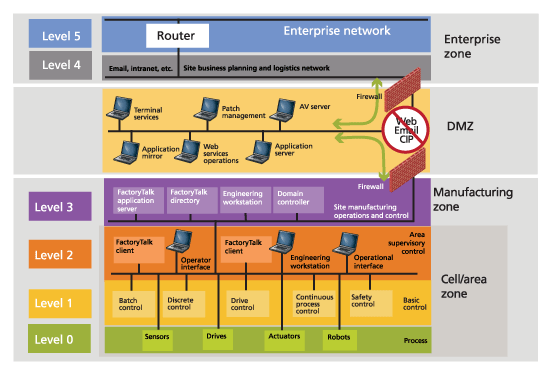
Figure 1. The Purdue Model
An example of an area where training can be helpful in risk mitigation is in teaching staff how to spot suspicious emails. Booz Allen Hamilton reports that spearphishing emails were the primary means of attack in 2015. Making sure people are aware that emails can be dangerous, helping them know what clues to look for, and that emails that seem odd should be reported, is the first line of defense against spearphishing. Activities such as email and internet browsing should be restricted to the IT network, but preventing them on the IT network altogether is a good step toward keeping threats from spreading to the OT network.
An incident response plan is an excellent tool for effective responses to malicious attacks. Things that might be included in such a plan include who to call in case of an intrusion, network and data flow diagrams, logging information, etc. Any affected devices should be immediately isolated from the network and the internet until they can be assessed. It is also important to know how to not tamper with potential evidence.
There are many benefits that can be derived from connecting the OT network to the IT network such as data collection and system monitoring. It can provide insight into how the ICS is operating and how it can be improved. When making this connection, however, a plan should be laid out and the risks identified. The network should be properly segmented to prevent an intrusion from easily spreading to other parts of the plant, an incident response plan should be defined, and personnel should be informed of the plan. Only then will your ICS be “more secure”.

